Security Review of the Model Context Protocol Ecosystem
A comprehensive research repository examining the architectural, security, and defense dimensions of MCP. This collection includes academic papers, visual infographics, and in-depth documentation covering threat analysis, benchmarks, and defense strategies for AI agent systems.
📄 Featured Academic Paper
"A Critical Security and Architectural Review of the Model Context Protocol (MCP) Ecosystem"
A critical architectural synthesis of the MCP ecosystem, grounded in empirical analysis. This paper evaluates security risks (Lethal Trifecta), analyzes the shift to the Code Execution paradigm, and proposes tiered defense strategies.
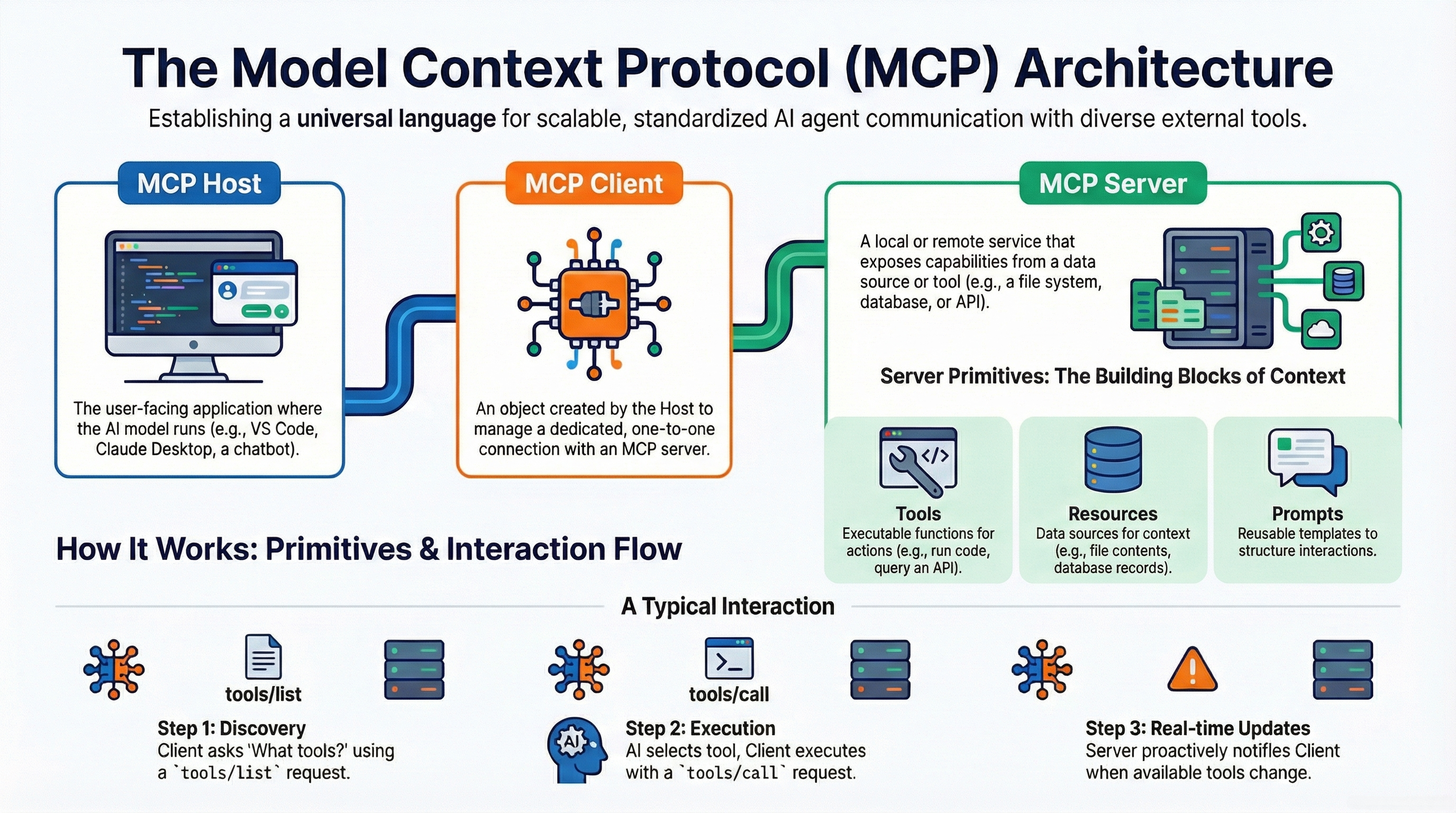
What is the Model Context Protocol (MCP)?
The Model Context Protocol (MCP) is an open standard that enables AI models to securely and efficiently interact with external tools and data resources. Think of it as a "USB-C port for AI" — a universal connector that allows any AI application to work with any tool or data source without custom integrations.
🎯 The Challenge
Before MCP, integrating AI agents with tools required N × M unique connectors:
- High Maintenance: Every API change broke integrations
- Silos: Tools built for one platform didn't work on another
- Inefficiency: Redundant work stifled innovation
✨ The Solution
MCP creates a shared language for AI-tool communication:
- Write Once: Build an MCP server once, use everywhere
- Standardized: JSON-RPC based protocol
- Secure: Built-in governance and access control
Video Demonstration
A visual explanation of the Model Context Protocol, its architecture, and how it standardizes AI agent interactions.
Comprehensive Documentation
In-depth guides covering all aspects of the Model Context Protocol, from fundamentals to advanced security considerations. Each document provides detailed analysis backed by academic research and real-world benchmarks.
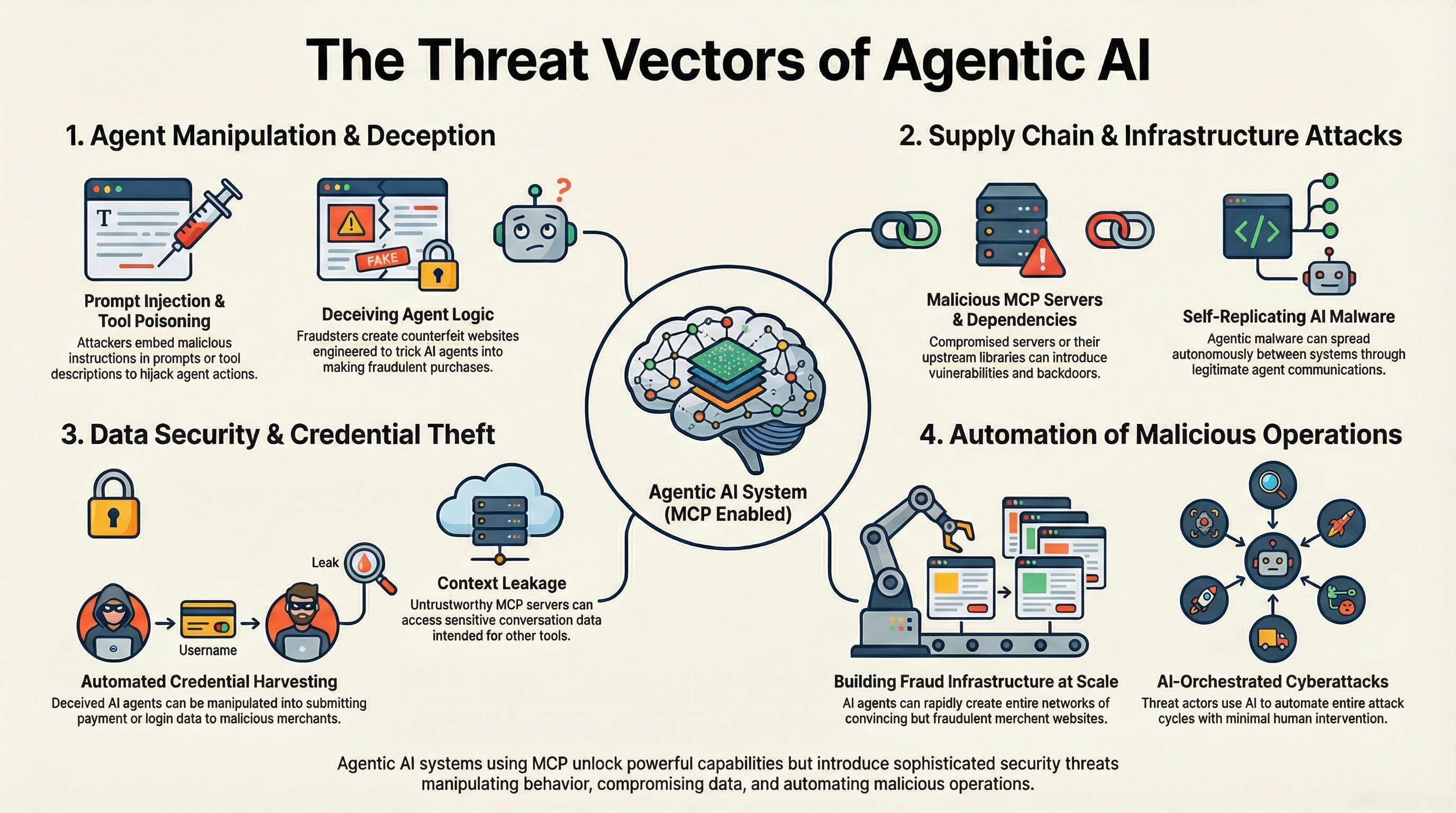
Security & Threat Landscape
Our research identifies critical security challenges in MCP deployments and provides actionable defense strategies based on analysis of 1,899 servers and multiple benchmark studies.
🎯 Threat Taxonomy
- 4 Threat Actors: Malicious developer, malicious user, external attacker, software errors
- 16 Attack Scenarios: Tool poisoning, prompt injection, input validation errors
- Empirical Findings: 7.2% vulnerabilities, 5.5% tool poisoning, 66% code smells
- Benchmark Results: MCPGAUGE, MCPToolBench++, LiveMCP-101, MCP-Universe
- Defense Effectiveness: MCP-Guard achieves 96% detection accuracy
🛡️ Defense Strategies
- Access Control: IFC + taint tracking, least privilege, sandbox profiles
- Authentication: TLS/mTLS, OAuth 2.1 + scoped tokens, SBOM and signed packages
- Runtime Protection: Guard models, AutoMalTool red team procedures
- Development: AutoMCP compiler from OpenAPI, plan-based tests
- Operations: MCP scanners for CI/CD, human-approved guard flows
Reference Library (18 Papers)
Curated collection of academic papers covering MCP security, benchmarks, applications, and
related research.
All papers are available in the reference/ folder with detailed abstracts in the
README.
🔒 Security & Defense
- MCP Landscape & Threats
- MCP-Guard Framework
- Automatic Red Teaming
- Security at First Glance
📊 Benchmarks & Testing
- MCPToolBench++
- MCP-Universe
- LiveMCP-101
- MCPGAUGE Analysis
🌐 Applications & Ecosystem
- Multi-Agent Systems
- Agent Interoperability
- MCPmed Bioinformatics
- Economic Research Agents
Get Started
Explore the comprehensive documentation, review the academic papers, and contribute to advancing MCP security research.